Why exploitation planning determines project success in competitive funding landscapes
In the realm of research project management, few concepts are as misunderstood yet critically important as “exploitation.” While researchers naturally focus on generating novel findings and advancing scientific knowledge, funding agencies increasingly demand clear pathways to practical application and societal value. Exploitation—the strategic process of transforming research outputs into tangible benefits—has evolved from a grant application checkbox into a fundamental determinant of project success and long-term impact.
As a science park specializing in research project management, we’ve witnessed firsthand how projects with robust exploitation strategies consistently outperform those treating it as an afterthought. This article explores why exploitation matters, how to develop effective strategies, and what evaluators truly seek when assessing exploitation potential.
Understanding Exploitation: Beyond Commercialization
In the context of research projects, exploitation refers to the systematic utilization of project results to create value beyond the research itself. Critically, exploitation encompasses far more than commercial activity—it represents any pathway through which research outputs generate benefits for society, economy, science, or policy.
Core Definition: Exploitation is the strategic process of leveraging research results—whether knowledge, technologies, methodologies, data, or networks—to generate tangible benefits for defined stakeholders through sustainable mechanisms that extend beyond the project’s funded lifetime.
This definition reveals several crucial aspects often overlooked:
- Strategic process: Exploitation requires deliberate planning, not spontaneous occurrence
- Multiple result types: Not only technological innovations but also methodologies, datasets, training programs, and policy frameworks
- Defined beneficiaries: Clarity about who benefits and how
- Sustainability: Mechanisms that persist after funding ends
- Tangible outcomes: Measurable impacts, not just potential applications
The Exploitation Spectrum: Four Primary Pathways
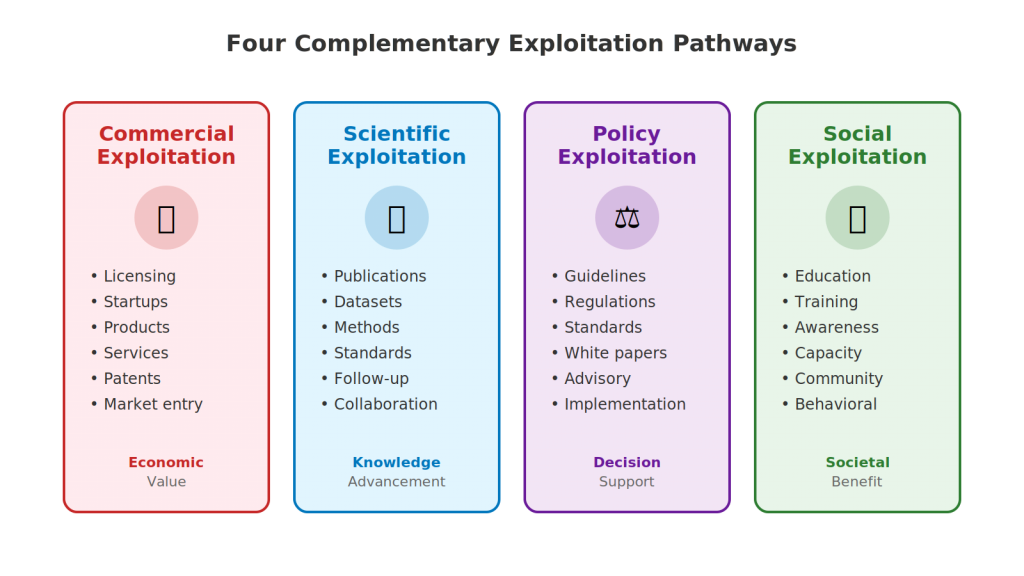
Successful projects typically pursue multiple exploitation pathways simultaneously, recognizing that different outputs suit different routes and that diversification increases overall impact probability.
Why Exploitation Determines Project Success
The prominence of exploitation in evaluation criteria reflects a fundamental shift in research funding philosophy. Agencies no longer fund research merely to expand academic knowledge—they invest in research to address societal challenges, strengthen economic competitiveness, and improve quality of life. Exploitation represents the mechanism translating research investment into these outcomes.
The Evaluation Reality
In Horizon Europe and similar frameworks, exploitation considerations permeate multiple evaluation dimensions:
Impact Criterion (Horizon Europe): Proposals must demonstrate “credible pathways to impact” including “concrete measures to disseminate results to multiple stakeholders and put them to use.” Exploitation plans directly address this requirement, often determining whether projects score above the evaluation threshold.
Evaluators consistently report that weak exploitation sections are among the most common reasons for proposal rejection, even when scientific excellence is high. Why? Because without clear pathways to application, research remains theoretical exercise consuming public funds without delivering promised returns.
Beyond Evaluation: Practical Benefits
Robust exploitation planning benefits projects throughout their lifecycle:
- Strategic coherence: Exploitation plans force clarity about what success looks like beyond publications
- Partnership quality: Attracts partners with genuine interest in outcomes rather than just funding
- Resource optimization: Guides work package design to ensure exploitable outputs
- Risk management: Identifies commercialization barriers or adoption challenges early
- Sustainability: Creates mechanisms for impact after funding ends
- Follow-on funding: Demonstrates trajectory toward larger initiatives or market readiness
Developing Effective Exploitation Strategies
Creating credible exploitation plans requires systematic analysis across multiple dimensions. The most successful approaches follow a structured methodology:
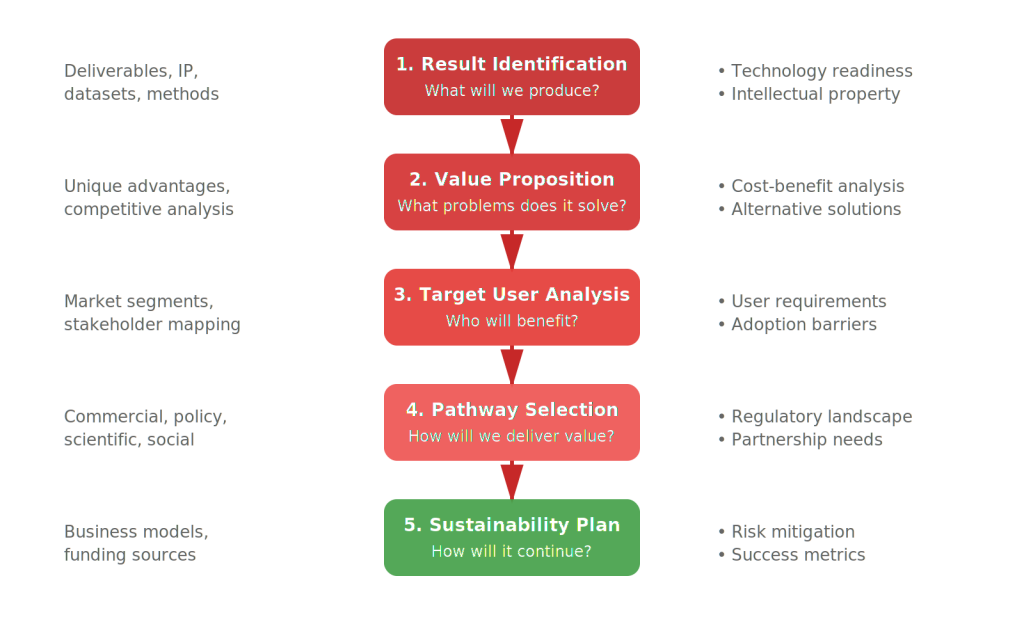
Exploitation Strategy Development Process
Step 1: Result Identification
|
Step 2: Value Proposition
|
Step 3: Target User Analysis
|
Step 4: Pathway Selection
|
Step 5: Sustainability Plan
|
Step 1: Result Identification and Classification
Begin by systematically cataloging all potential project results:
| Result Type | Examples | Typical Exploitation Routes |
|---|---|---|
| Technological innovations | Prototypes, algorithms, devices, software | Licensing, spin-offs, patents, products |
| Knowledge and insights | Research findings, data analysis, evidence synthesis | Publications, databases, policy briefs |
| Methodologies and tools | Assessment frameworks, protocols, analytical techniques | Standardization, training programs, SaaS |
| Data assets | Datasets, biobanks, registries | Open repositories, controlled access, services |
| Networks and communities | Collaborative structures, user groups | Associations, platforms, follow-on projects |
| Trained personnel | PhD graduates, skilled technicians | Employment, consulting, teaching |
For each result, assess its Technology Readiness Level (TRL) or equivalent maturity indicator, as exploitation strategies differ dramatically between early-stage concepts (TRL 1-3) and near-market solutions (TRL 7-9).
Step 2: Value Proposition Analysis
Articulate precisely what problem each result addresses and for whom. Strong value propositions exhibit three characteristics:
- Specificity: “Reduces diagnostic time by 40%” not “Improves healthcare efficiency”
- Quantification: Measurable benefits (time saved, cost reduced, accuracy improved)
- Differentiation: Clear advantages over existing alternatives
Common Pitfall: Describing features rather than benefits. “Our platform uses machine learning” is a feature. “Our platform enables clinicians to identify rare diseases 6 months earlier than current practice, potentially saving €50,000 per patient in treatment costs” is a value proposition.
Step 3: Target User Analysis
Move beyond generic stakeholder lists to detailed user segmentation:
- Primary users: Direct beneficiaries who will actively use results
- Decision-makers: Those authorizing adoption or purchase
- Influencers: Opinion leaders shaping acceptance
- Gatekeepers: Regulatory or approval authorities
- Economic buyers: Those funding acquisition or implementation
For each segment, understand:
- Current practices and pain points
- Decision criteria and procurement processes
- Barriers to adoption (technical, economic, cultural, regulatory)
- Information sources and trusted channels
Step 4: Pathway Selection and Strategy Formulation
Based on result characteristics and user analysis, select appropriate exploitation pathways. Effective strategies typically combine multiple routes:
Commercial Exploitation Strategies
- Direct commercialization: Consortium partners bring products/services to market
- Requires: Market access, manufacturing capability, regulatory expertise
- Timeline: 2-5 years post-project typically
- Licensing: Transfer IP rights to external entities for development
- Requires: Robust IP protection, attractive terms, licensee identification
- Timeline: Can begin during project for mature results
- Spin-off creation: Establish new company to exploit results
- Requires: Entrepreneurial talent, seed funding, support infrastructure
- Timeline: 1-3 years for formation, longer for market success
- Joint ventures: Partner with industry for co-development
- Requires: Complementary capabilities, aligned incentives, governance
- Timeline: Variable, often begins mid-project
Scientific Exploitation Strategies
- Open publication: Disseminate through peer-reviewed channels
- Data repositories: Make datasets FAIR (Findable, Accessible, Interoperable, Reusable)
- Standardization: Contribute methods to ISO, CEN, or domain-specific bodies
- Follow-on research: Secure additional funding for next development stages
- Training programs: Transfer methodologies through courses or workshops
Policy Exploitation Strategies
- Policy briefs: Translate findings into decision-maker formats
- Advisory engagement: Join technical committees or expert panels
- Guideline development: Work with professional associations on practice standards
- Regulatory dialogue: Engage authorities on framework updates
- Evidence synthesis: Provide systematic reviews for policy decisions
Social Exploitation Strategies
- Educational resources: Develop materials for schools or public education
- Capacity building: Train practitioners in underserved regions
- Community platforms: Establish user networks for peer support
- Awareness campaigns: Promote behavior change or stigma reduction
- Citizen science: Engage public in ongoing data collection or monitoring
Step 5: Sustainability Planning
The most critical yet frequently neglected component: how will exploitation continue after project funding ends?
Sustainability Imperative: Evaluators specifically assess whether exploitation activities have viable post-project continuation mechanisms. Projects proposing activities that collapse when EU funding stops are unlikely to score well on impact.
Robust sustainability plans address:
- Financial sustainability: Revenue models, follow-on funding sources, cost recovery mechanisms
- Organizational sustainability: Which entity maintains results? What governance structure?
- Technical sustainability: Maintenance, updates, user support provisions
- Community sustainability: How user engagement continues and grows
Intellectual Property: The Exploitation Enabler
Intellectual property (IP) strategy forms the foundation of commercial exploitation. Yet IP management in collaborative research projects presents unique challenges requiring careful navigation.
Key IP Considerations for Exploitation
- Background vs. Foreground IP:
- Background: Pre-existing knowledge partners bring
- Foreground: New IP generated during project
- Clear delineation prevents exploitation barriers
- Ownership allocation:
- Default: Creator owns (organization employing inventor)
- Joint ownership: Requires unanimous agreement for exploitation (problematic)
- Strategy: Align IP ownership with exploitation capability
- Access rights:
- Consortium partners typically retain access rights to foreground IP
- Can complicate exclusive licensing or spin-offs
- Negotiate fair compensation mechanisms
- Protection strategy:
- Patents: For novel inventions with commercial potential
- Trade secrets: For process knowledge or algorithms
- Copyright: For software, databases, creative works
- Trademarks: For products, services, or brands
Strategic Principle: IP protection should serve exploitation goals, not vice versa. Patenting everything regardless of commercial viability wastes resources. Conversely, failing to protect high-value innovations can prevent exploitation entirely.
Measuring Exploitation Success
Effective exploitation requires tracking appropriate metrics throughout project lifecycle and beyond:
During-Project Indicators
- IP filings (patents, trademarks) relative to plan
- Industry engagement (collaborations formed, MOUs signed)
- Investment attracted (VC interest, licensing negotiations)
- Policy uptake (citations in white papers, advisory roles)
- User adoption (downloads, pilot implementations, training participants)
Post-Project Indicators
- Commercial: Revenues generated, products launched, jobs created, market share
- Scientific: Citations, method adoption rate, standard integration
- Policy: Guideline implementations, regulatory changes, practice uptake
- Social: Behavioral changes, capacity built, community growth
Realistic Timelines: Commercial exploitation often requires 3-10 years post-project. Scientific exploitation may occur faster but policy change typically takes longer. Set realistic KPIs acknowledging these timescales.
Common Exploitation Pitfalls and How to Avoid Them
Pitfall 1: Technology-Push Thinking
Problem: “We’ll build this amazing technology and users will come” Solution: Begin with user needs. Involve target users from project start to ensure solutions address real problems.
Pitfall 2: Vague Exploitation Plans
Problem: “We will commercialize through licensing or spin-offs” Solution: Specific routes with named responsible partners, timelines, and success criteria. If uncertain at proposal stage, describe decision criteria and process.
Pitfall 3: Ignoring Regulatory Requirements
Problem: Developing medical devices without CE marking pathway Solution: Engage regulatory experts early. Budget for compliance activities. Understand approval timelines and requirements.
Pitfall 4: Underestimating Time-to-Market
Problem: Proposing market entry 6 months post-project for TRL 4 technology Solution: Realistic assessment of development stages required. Identify follow-on funding sources for commercialization phase.
Pitfall 5: Academic-Industry Misalignment
Problem: Universities prioritizing publications while industry partners expect exclusive IP Solution: Negotiate consortium agreement clarifying publication rights, IP ownership, and exploitation responsibilities before project start.
Pitfall 6: No Identified Exploiter
Problem: Every partner assumes someone else will commercialize Solution: Designate specific partners responsible for exploiting specific results. Include commitment in consortium agreement.
Pitfall 7: Treating Exploitation as Administrative Requirement
Problem: Exploitation section written to satisfy evaluators rather than guide action Solution: Integrate exploitation into project design. Review and update exploitation plans at every consortium meeting.
The Horizon Europe Perspective
Horizon Europe explicitly emphasizes exploitation through multiple mechanisms:
- Impact criterion weight: Impact typically accounts for 30-40% of evaluation score
- Open Strategic Autonomy: Preference for exploitation enhancing European competitiveness
- Mission-orientation: Exploitation must demonstrate contribution to defined societal goals
- EIC Accelerator: Dedicated funding for high-potential commercialization
- Exploitation monitoring: Post-project tracking of commercial outcomes
Evaluator Expectation: “We look for exploitation plans that are specific, realistic, and ambitious. The best proposals demonstrate that partners have genuinely thought through how to get from research output to real-world application, including acknowledging challenges and articulating mitigation strategies. Generic statements about ‘seeking commercialization opportunities’ score poorly.”
Building Exploitation Capability: Organizational Perspective
For research organizations consistently participating in funded projects, developing institutional exploitation capability delivers competitive advantage:
- Technology transfer offices: Professional support for IP management, licensing, spin-off creation
- Industry liaison: Maintained relationships with potential exploiters
- Entrepreneurial training: Programs developing commercialization skills among researchers
- Seed funding: Internal resources for proof-of-concept or prototype development
- Networks: Connections to investors, accelerators, industry partners
- Track record: Documented exploitation successes strengthening future proposals
Conclusion: Exploitation as Success Catalyst
In contemporary research funding, exploitation has evolved from optional add-on to core requirement. This shift reflects legitimate expectations that publicly funded research should generate public benefit—not just academic outputs but tangible improvements to economy, society, health, and environment.
Projects treating exploitation strategically—as integral to design rather than afterthought—consistently outperform those treating it as administrative burden. They secure better funding scores, attract stronger partners, achieve greater impact, and generate sustainable benefits extending far beyond project duration.
For science parks and research support organizations, expertise in exploitation planning represents valuable differentiation. By helping researchers translate scientific excellence into practical value, we bridge the gap between discovery and application—fulfilling the ultimate purpose of research funding.
Strategic Imperative: As funding competition intensifies and impact expectations rise, exploitation capability increasingly determines which organizations and projects succeed. Investing in exploitation planning expertise—whether through internal capability building or expert partnerships—is no longer optional but essential for research success in the 2020s and beyond.
The question is no longer whether exploitation matters, but how well your organization can demonstrate credible pathways from research to impact. The answer may well determine your next project’s success.
